Cyber Security e infrastrutture critiche
Attività reattive e proattive per infrastrutture critiche
 Segui
Segui Contatta l'autore
Contatta l'autoreCentro di Ricerca di Cyber Intelligence and Information Security (CIS) - La Sapienza - Università di Roma
 Segui
Segui(PDF in lingua inglese)
Standards for Cyber Security
Basic activities
Common questions
Common issues
Claims
Standards for Cyber Security
- Common Criteria
- Framework (NIST & Nazionale) per la Cyber Security e la Data Protection
- Italian CIS National Cybersecurity Framework
- EU Cybersecurity Act
-- Security assessment
-- Security by design
-- Best practices
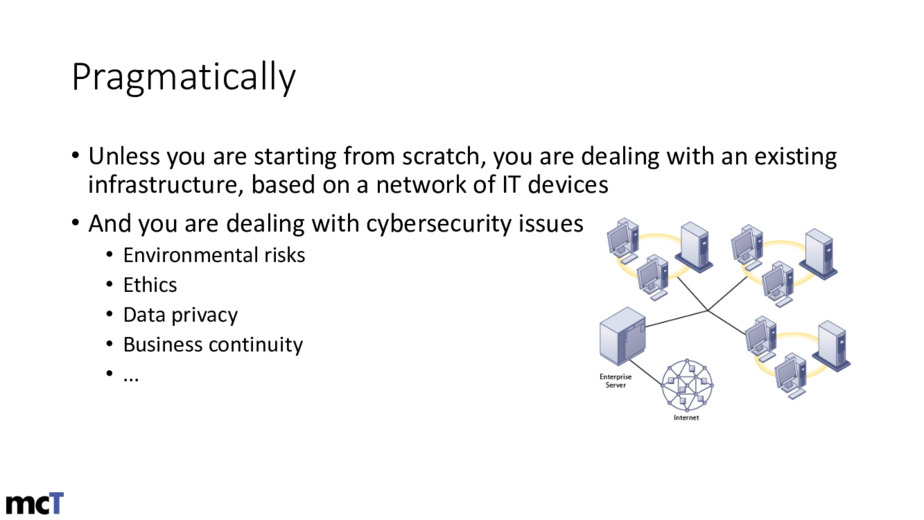
Pragmatically
Unless you are starting from scratch, you are dealing with an existing infrastructure, based on a network of IT devices
And you are dealing with cybersecurity issues
- Environmental risks
- Ethics
- Data privacy
- Business continuity
Basic activities
One needed step is to take a picture of your data
- Network
- Business
- Relationships among business activities and devices
- Weakness
The focus of this talk is on weakness
Why weakness ?
- To date, hundreds of thousands known and cataloged cyber vulnerabilities exist
- Documented in the American NVD (National Vulnerability Database) CVE (Common Vulnerabilities and Exposures)
- Together with a severity score (CVSS) ranging between 0 and 10 (plus several subscores)
- Known by both defenders and attackers
A very simple idea (neglecting the details)
It is very likely that attackers will use your weaknesses !
It is a good idea analyze them and prepare some countermeasures to:
- Reduce the weaknesses
- Be ready to defend yourselves
Very complex in real cases
- A network of computers is affected by hundreds/thousands of vulnerabilities
- And attacks are typically composed by a sequence of steps
- Multistep attack
Video Webinar
Settori: ,
Parole chiave: ,